In September of 2024, Microsoft released Windows 11, version 24H2. Within this version, there is a new feature in the Printers and Scanners configuration called Windows Protected Print mode. What is this feature and what does it do, you might wonder?
Microsoft has been inundated with bad press for many years around ongoing security and stability issues. One of the areas that has long been at issue is the topic of Windows printing. To those charged with administering print in organizations, the Windows print spool has appeared to be fickle and unreliable. This is because the Windows spool would often hang or crash, killing printing for a time, causing document loss and other such print frustrations. And anyone who’s seen the movie Office Space knows how that story ends.
Let’s be clear: Microsoft developers were likely not the source of these problems. Hundreds of different third-party print drivers were used in this environment and were often (maybe always) the source of the instability. Further, for the print process to work at all, the Windows spooling processes had to run with a lot of authority. This gave rise to the PrintNightmare exploit and may have opened the door to other attack vectors.
What is a Windows Print Driver?
So, what is a print driver, anyway? This question has a long and complex answer, but the simple way of saying it is that the driver takes the graphical screen data that a user can see and translates it into the language of the printer. Then, by using certain Windows network abilities, the driver sends the data to the device. There are many things associated with this basic concept having to do with where this rendering occurs (server or workstation) shared devices, device-specific capabilities like duplex and color, and many others. Since printer manufacturers know how to talk to their own printers, Microsoft allowed for third party drivers to make that happen.
As Windows grew in popularity, tens of thousands of developers started writing drivers. This meant an exponential growth in risk since drivers didn’t age well, while Windows continued to move forward. Windows went from a 32-bit to a 64-bit operating system back in 2005, but drivers were slow to follow. In fact, there are still many 32-bit drivers running in the real world that are 25 years old or more. Users and print vendors demanded that Microsoft stay backward compatible to protect old investments and, perhaps to their peril, they did.
Microsoft has attempted many times to force the hand of those running old code. In 2009, Microsoft introduced XPS as a better way of dealing with the rendering issue in the Windows spool. The hope was that print vendors would adopt XPS rather than the wide range of languages for rendering.
At that time, PCL, PostScript, Prescribe, ZPL, IPDS and many other data streams were used throughout the industry. Printer manufacturers balked at Microsoft’s approach and instead allowed XPS input into their drivers but rendered locally anyway. This allowed hardware vendors to differentiate themselves from each other making their own products more desirable.
Microsoft certified certain drivers via Windows Update. Windows signed drivers to certify that they were ok. Still the problems persisted.
Given PrintNightmare and all the bad security press that Microsoft had received on printing issues, it is understandable that they gave up. Enter Windows Protected Print mode (WPP).
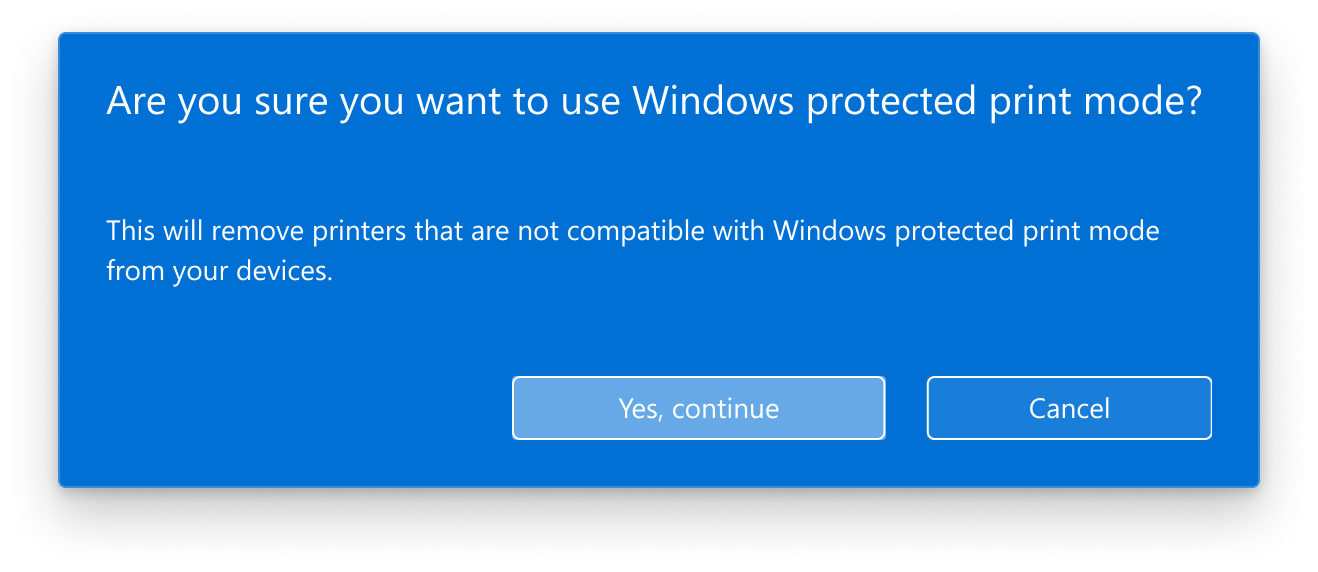
Windows Protected Print mode in Action
When WPP is turned on, several interesting things occur. See this link for the best detailed explanation of exactly what happens. Then read on for the potential implications.
In short, when implementing WPP, all third-party drivers are removed. All printers that used these drivers are removed. Printer processes are “demoted,” meaning that they only run with the authority of the logged-on user. As to defining new printers, there are only two ways to do this. One is to use Microsoft Universal Print, and the other is to use Mopria certified devices that can be discovered on the network.
For your Windows 11 24H2 machine to find a Mopria printer (if you have any), it must be either discoverable on the local network segment via WSD mechanisms, or you must have the hostname / IP address of the printer. Easy enough for home users or very small businesses, but for an enterprise with 10,000+ devices, this could be a problem. Further, many LRS customers are removing printers from any internal network… meaning that no workstation can talk to a printer in any way.
Those of you that have been at this a while might consider the use of a Windows Print server to get around this. But maybe not. Windows Server 2025 is not yet released, but early indications are that this is also on Build 24H2 with WPP available. If WPP is enabled by policy in an organization on all servers and workstations, then there can be no shared devices. Mopria printers are IPP by definition and Windows has never allowed for sharing of an IPP device. (Logically, they are already shared if they are on the network, right?)
Real-World Implications
Let’s think about this in terms of an enterprise, for example, your nearby hospital. Many modern Electronic Health Record systems (EHR or EMR systems) count on Windows server printing and Windows shares today. In fact, almost all of them use standard Windows printing. Thinking of other industries, many ERP systems also count on Windows print servers and Windows shares. And what about label printers – the heart and soul of getting patients and products out the door? These will not be available.
That’s bad enough. But even worse to consider is that Microsoft intends on having WPP turned on by default in 2027. Imagine having to change your entire fleet of devices, upgrade all of your applications, and being ready in two short years. Think of the wide array of applications that run on servers, in the cloud, and on local workstations that will need to be tested and likely upgraded. (No really – think about it.)
How can you future-proof your print environment today while addressing the problems WPP is meant to fix?
I’ve been telling you how to do this for years. LRS processes directly capture print from Windows as soon as it’s rendered on a local machine. Your workstations are already safe if you use LRS methods and software. There is no need to turn on WPP if you use the Personal Print Manager component of the LRS solution. There is no need to rush into changing your fleet. You are protected today.
LRS is looking at how to deal with the existence of WPP in the long run. Since we have done IPP and IPPS printing since 2004 (both incoming and outgoing) and have long tried to eliminate our dependence on operating system spooling of any kind, we are confident that we can work hand in hand in the future – with or without WPP.
As we have been since 1979, LRS is here for you.